How to Hack a Phone: The Beginner-Friendly Guide
HACK A CELL PHONE
Fill in your target's phone number here and our tool will see if this phone is hackable!
Gathering data...
HACK A CELL PHONE
SEE HACKED PHONE DATAEvery person today owns a smartphone, often leading to them interacting with dangerous people or even being unfaithful in their relationships and marriages. So, how to hack a phone? And why?
Whether you’re a concerned parent or a partner, there might be several situations in which you might want to hack into someone’s phone to see who they speak to on their social media accounts. If you’re wondering how to do so, this guide is for you.
However, all these methods can also hack into your device. This guide explores various ways a phone can be hacked and how you can protect your phone from being a victim of someone exploiting security vulnerabilities.
DISCLAIMER: This article is for educational purposes only. Some methods discussed in this article are illegal, especially when used without the user’s consent. Always check your local laws to ensure you don’t land into legal trouble.
How to Hack Someone’s iPhone Remotely for Free?
The most reliable method is purchasing an app to hack into someone’s phone for free instead of opting for ”free” online solutions because there isn’t a free, reliable method. Many online tools can be used to steal the sensitive data stored on your device or any connected accounts.
Although many websites offer free hacking features, they are scams, or you don’t want to install malware on your devices. As a general rule, you should stay clear of these websites. The only working method of accessing someone’s phone is by using spy apps. However, they do require you to purchase a subscription plan.
mSpy
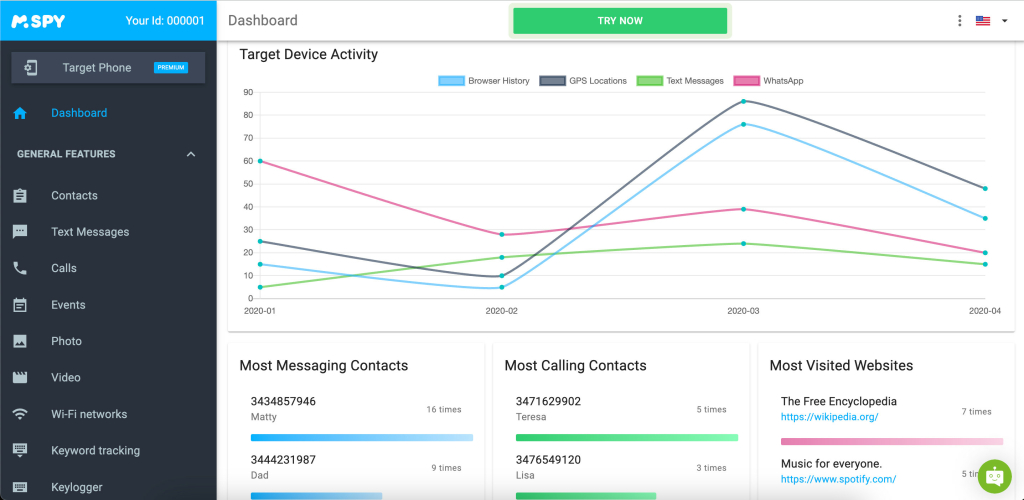
The first and best spy app you can use to hack into someone’s cell phone is mSpy. This app is compatible with Android and iOS mobile devices and can even be installed remotely. It offers plenty of features, a lot of which don’t require you to root or jailbreak your device.
Some of the key features of this app include:
- A phone call and text message monitoring;
- Keystroke and keyword tracking;
- GPS location tracking;
- Monitoring media files like images and videos;
- Monitoring social media accounts.
Pros
- Plenty of tracking features
- Offers remote access for installation on iOS
- 100% invisible in Stealth Mode
- Easy to install and use
Cons
- Only monitors one device per account
- Advanced features require rooting and jailbreaking
eyeZy
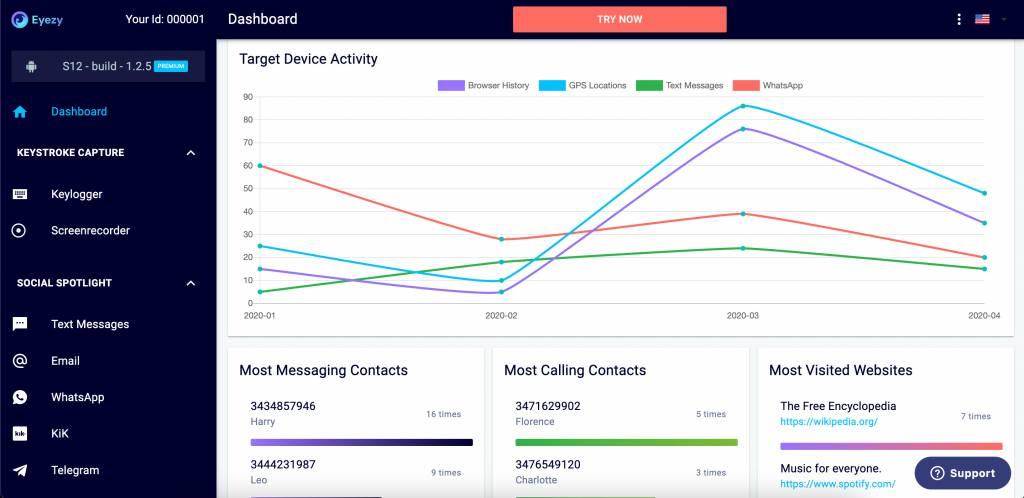
The second app on this list that you can use to hack cell phones is eyeZy. Like mSpy, it’s compatible with Android and iOS devices and doesn’t require rooting or jailbreaking for its basic features. It has plenty of features, such as monitoring text messages, locations, etc.
This app is ideal if you’re wondering how to hack someone’s iPhone remotely. A comprehensive list of its features includes:
- Monitoring chats and media on online accounts like Facebook, Snapchat, Instagram, and more;
- Monitoring text messages and incoming and outgoing calls;
- GPS location tracking and geofencing;
- Web browser history monitoring;
- Stealth Mode;
- Remotely blocking websites, WiFi networks, and applications;
- Tracking keystrokes and other sensitive data.
Pros
- Monitors all major social media applications
- Easy to install on the target device
- Completely invisible in Stealth Mode
- Works on an iOS and Android device
Cons
- Doesn’t offer a free trial
- No remote installation for Android target devices
How to Hack a Mobile Phone with a Phone Number?
The process is quite easy if you hack someone without touching their phone. We’ll explain everything below in detail. One great spy app to keep an eye on is Cocospy.
Here’s how you can use Cocospy to learn how to hack someone’s cell phone without touching it.
For Android
Although most functions can be performed without touching it, you will still need to obtain one-time physical access to the device to install the software.
You need to purchase a subscription plan → sign up for an account → download the installation file → install it on the desired phone
If you’ve wondered how to hack an Android phone from a computer remotely – Cocospy has your back too. You can access all phone files through their user control panel on your PC.
The process generally takes less than five minutes, and the app will run silently in the background. This makes it nearly impossible for the target device to know they’re being spied on.
For iPhone
If your target has an iOS device, the process is much more comfortable and can be performed remotely.
However, to hack an iPhone you will have to obtain access to the target’s iCloud account password and other credentials.
Then, you can enter their credentials in the spy app and get full access to their device. Let’s use Cocospy as an example again.
Cocospy uses this data to create a clone of their phone, enabling you to monitor all iPhone activities. These remote features make Cocospy a great phone spy app for Android and iPhone.
How to Hack iPhone Remotely?
If you want to hack a phone, it takes a few easy steps to hack someone’s iPhone remotely using Cocospy. As already noted, to hack a phone without touching it, you need to use an iPhone.
In this section, we show you the steps involved in hacking an iPhone:
Step 1: Visit the official Cocospy website to register for the service. While at it, choose a plan that suits your hacking needs.
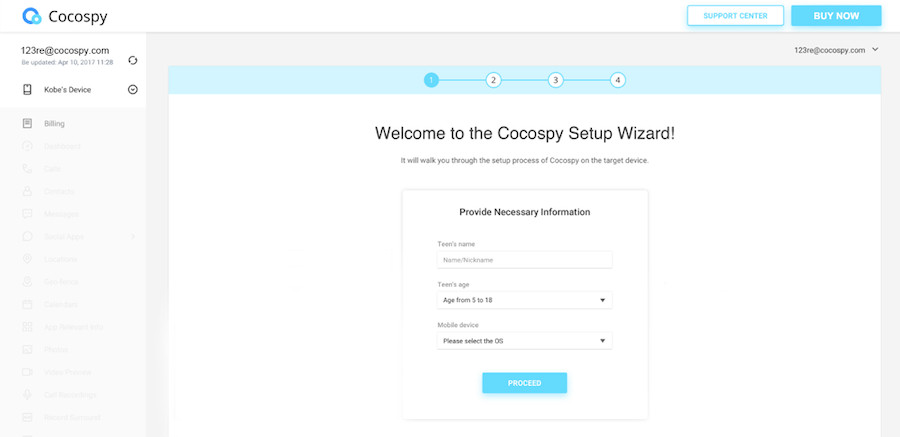
Step 2: Choose the operating system and device you want to hack. In this case, iOS.
Step 3: To set up the device, you need to provide the iCloud credentials of the target device. After delivering them, click the Verify button.
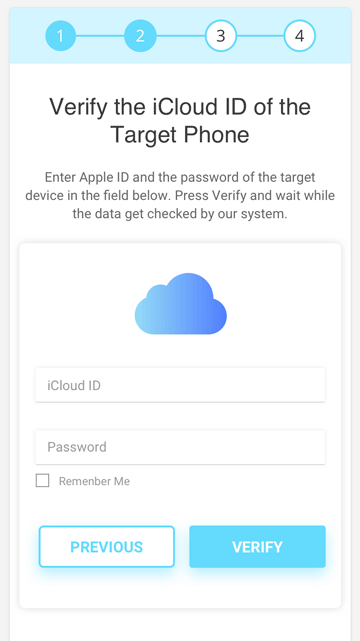
Give the software a few minutes to sync all the data.
Step 4: After syncing the data from the target iPhone, click the Finish button to exit the setup.
Step 5: Log in to your Cocospy dashboard to start hacking your target device.
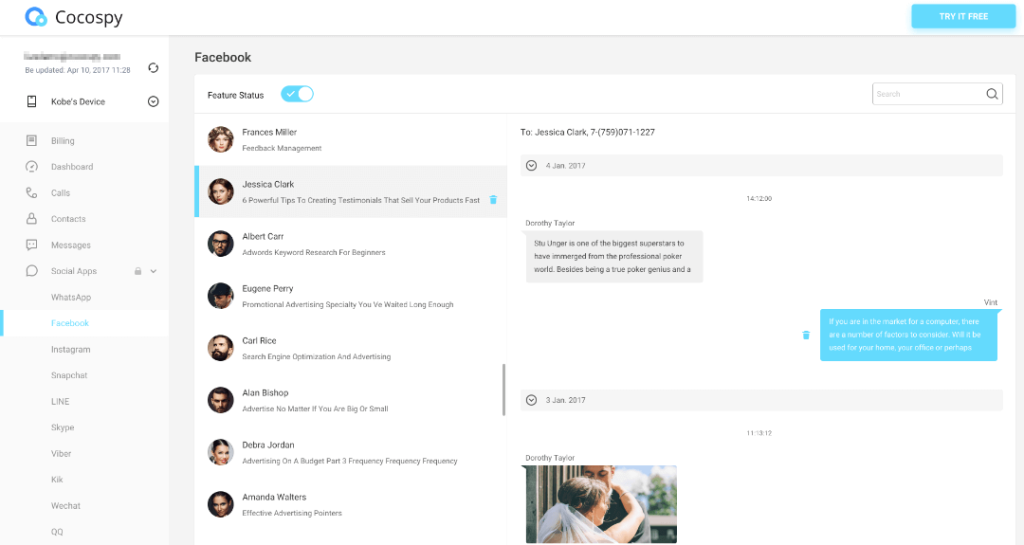
Cocospy allows you to access virtually every aspect of the target iPhone.
It will enable you to learn your target’s whereabouts, online activities, and chats in one place.
Is It Possible to Hack Into the Phone Without Touching It?
Although hacking a phone remotely or only by knowing the victim’s phone number is possible, it is not easy to perform.
There isn’t a universal free phone tracker or a hacking app that will give you access to anything and everything.
If you’re an advanced computer user who knows how to write programs, you can utilize more sophisticated methods to achieve your goal. We will discuss some of them later on in the article.
On the other hand, if you’re a beginner, using ready-made software might be a better and more effective option. It does what any other hacking tool would do – it allows you to read someone’s text messages, see their social media, track their location, etc.
However, remember that most of these tools and techniques require physically accessing the device.
How to Hack a Phone Number with a Keylogger?
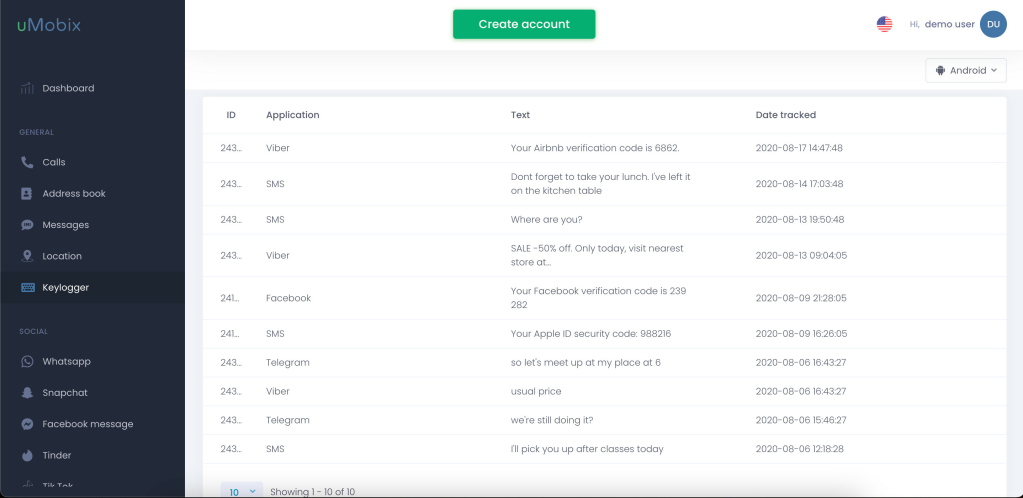
A keylogger is comprehensive security software that can hack into a phone by bypassing its security features to get any information. uMobix is among the best keyloggers in the market. That works well on an Android and iOS cell phone and doesn’t require rooting or jailbreaking.
As a keylogger, uMobix tracks all the texts and passwords entered on the hacked phone and provides you with a report on the app’s dashboard. Other than using this app as a keylogger, it also has several other features, including:
- Monitoring text messages and phone calls, including deleted messages;
- Tracking all websites visited on the web browser;
- Monitoring social media apps along with full control over Facebook and Instagram on iOS;
- Monitoring media files stored on the device;
- Tracking app activity;
- Tracking the target’s GPS location, and more.
The important thing to note is that this app cannot be purchased from the Google Play Store or any third-party App Store. It can only be purchased from the uMobix website. The app also receives consistent software updates, so you’ll always have the latest version.
Pros
- User-friendly interface
- Affordable pricing
- Cannot be detected by antivirus software
- 100% undetectable
Cons
- Doesn’t come with geofencing
- Full Instagram and Facebook control is only available on the iOS operating system
How Do You Hack a Phone with Phishing?
If you’ve ever wondered how to hack someone’s phone without touching it free – phishing is the answer. So, how do phishing attacks work?
Phishing is one of the most popular ways to hack a phone because it doesn’t require physical access.
The target is contacted via email or SMS or malicious apps made to look like the real ones. The whole purpose is to make the target believe that your email is legitimate and to convince them to open a link that you’ve previously created.
That is usually done by impersonating a real company or organization. However, it takes some patience and attention to detail.
Here’s how to do it:
1. Decide which organization you’d like to impersonate.
- The most popular types include payment companies (PayPal, Payoneer), banks, etc.
2. Create a fake website that resembles the original as much as possible.
- Pay attention to grammar, punctuation, and other details because a single mistake can give you away. Make sure to include a login page.
3. Obtain the target’s mobile phone number or email
4. Create your email.
- Ensure that the username and the domain name are as close to the original as possible. For example, if you’re impersonating PayPal, buy a domain like pay-pal.net, pay-pal.org, etc.

5. Write an email or text saying urgent account action is required.
- You can say that the target’s account needs to be verified, that their account was hacked, or something similar.
6. Make sure to include a logo and other details to make it seem believable.
7. Include a login link.
- The goal is to have the victim open the link and enter their login credentials.
8. Send the email /text and wait for a response.
- If successful, the victim will have logged onto the fake website and entered their credentials. Since you’ve created the fake website, you won’t have to worry about two-factor authentication either.
9. use the obtained information to hack their mobile phones or access other accounts.
Bear in might, though, that your email might end up in the Spam folder, preventing the victim from opening it. Because of that, sending a text might be a better option.
Using Advanced Hacking Methods
On the other hand, there are a lot of other, more aggressive forms to hack a phone and access someone’s sensitive information, such as their bank accounts or passwords.
However, bear in mind that these attacks are for advanced users with prior coding experience, so not everyone can perform them. And these methods are so advanced that you can hack someone’s phone camera or even track their location.
Because this article is beginner-friendly, we won’t be going in-depth about how to carry them out. When it comes to advanced hacking tools, here’s what we’ll learn about:
- How to hack Android phones remotely using cloak and dagger attack – this method is for Android phones only;
- How to perform a control message attack;
- IMSI Catcher or Stingray cell phone hack;
- How to hack someone’s cell phone using the SS7 vulnerability;
- How to hire a professional hacker.
Midnight Raid Method
The midnight raids method is not precisely beginner-friendly, but non-advanced users can still make it work.
The process is rather easy, and all the hacking equipment you need is a Wi-Fi-enabled laptop, a WAP Push app, a data-retrieving softwaretwo phones.
One phone will act as a GSM modem for the laptop, while the other will receive information. This method is called “midnight raid” because it’s usually performed while the victim is asleep.
Here is how to hack a phone by using this method:
- Locate the targeted device.
- Send a text to the target’s phone, saying, “You’ve been hacked.” Just their number is needed.
- This message should be followed by a push message that prompts the victim to install “security software.” You will create that message by using the WAP Push message app.
- The push message is delivered in a way that triggers the browser. So, the victim doesn’t even need to click the malicious link.
- Once done, the process will begin. The data-retrieving app will provide you with the phone’s IMSI number, and a unique phone ID.
- You can also use the app to retrieve other information, such as the contacts list.
Cloak and Dagger Attack
Cloak and dagger attack is a newer form of exploitation that affects Android devices.
It works by installing malware as a malicious app and enabling it to fully control the UI feedback loop, giving unobstructed phone access. The phone user usually doesn’t notice that their phone is infected.
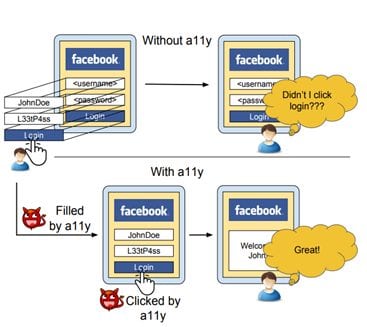
To be successful, this attack only requires two permissions.
Attackers can extract passwords, pins, and other sensitive information. To make the matter even worse, this exploit is still active, and no known fixes exist.
Control Message Attack
A control message attack is another advanced way to hack a phone, including sending a control message to the target device.
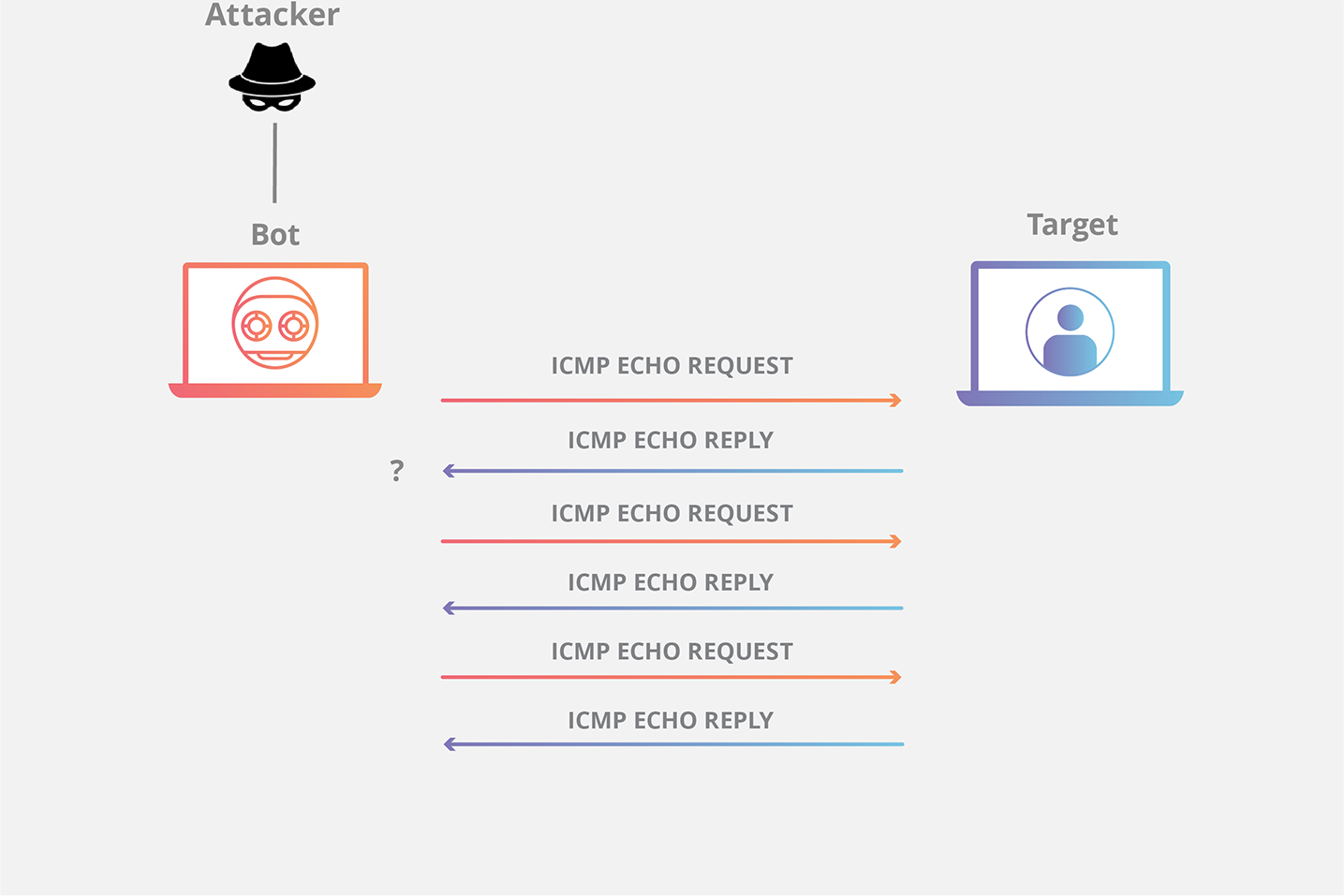
The control message travels over the GSM network and ends up in the victim’s phone connected to a Wi-Fi network.
Then, you can use dedicated toolkits to sniff internet traffic or uncheck SSL to make the device vulnerable.
So, if you’ve ever wondered how to hack a phone through Wi-Fi – this is precisely how you can do it.
IMSI Catcher or Stingray
IMSI Catcher or Stingray hacking prey on the weakness of security protocols found in smartphone operating systems. An Android phone can identify a cell tower through its IMSI number.
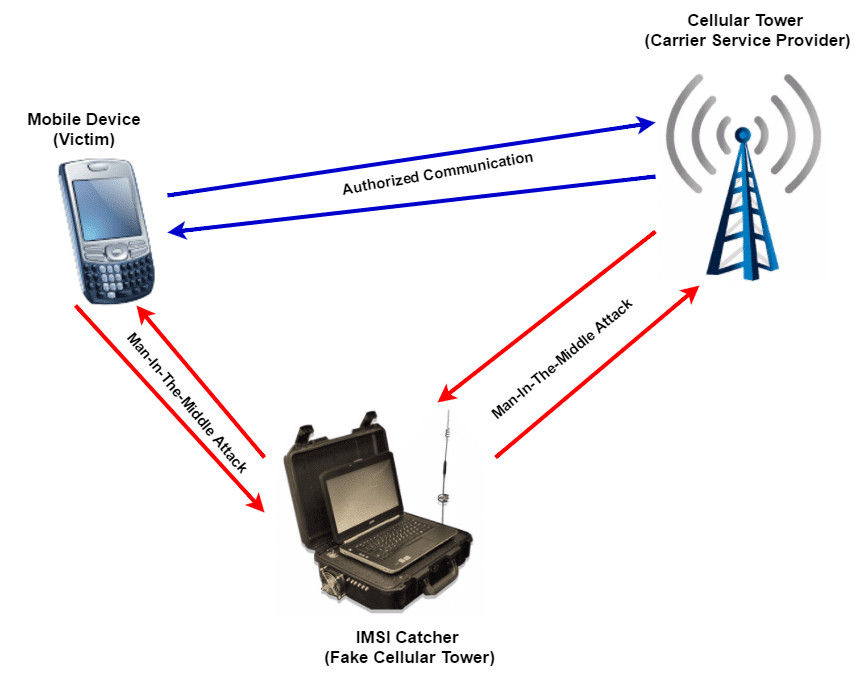
Since the phone always connects to the nearest tower, hackers can use this knowledge and set up false towers.
If a device connects to a fake cell tower, it is vulnerable to hacking and exploitation. This is a great way of learning how to hack someone’s phone remotely.
SS7 Mobile Tracking
If you want to know how to hack a mobile phone without free software, the SS7 vulnerability might be the answer. It enables hackers to intercept SMS messages, phone calls, and the user’s location.
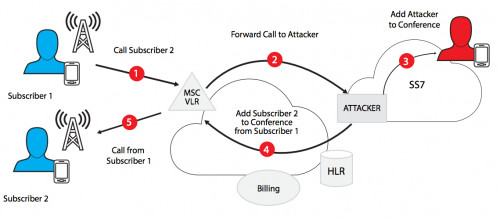
SS7 stands for Signaling System No 7, a mechanism connecting one call to another. It was discovered that SS7 has a vulnerability that hackers can exploit.
Namely, if they gain access to the SS7 system, they have the same access as security services.
How Can You Hack a Phone by Hiring a Professional Hacker?
Hiring a professional hacker is difficult because no hacker is allowed to advertise their services freely on the internet. Most of their activities are illegal, after all.
However, in theory, finding a hacker can usually be performed via the Dark Web or some cell phone hacking software forums.
Bear in mind, though, that you can never know whether some random person online is an actual hacker or whether they’re there only to take your money. So you must be careful before you hand over too much control or information to the wrong hands.
So, we strongly recommend not going this route. It bears more risks than benefits, and you might end up being the one who got hacked.
How to Remotely Hack a Samsung Phone?
The most common way to learn how to hack into someone’s phone remotely is by exploiting a security flaw in the device’s programming and installing a bug to gain access. The system bug method will let you hack the phone and find the necessary information for Samsung phones.
To exploit a system bug on a Samsung phone, you will need:
- The target Samsung device;
- A computer;
- USB cable;
- Debugging software (such as “SuperSU” or “KingRoot”);
- Patience!
Step 1: Ensure your target Samsung device is turned on and the screen is unlocked. Connect the USB cable to the phone and computer. On the computer, open up debugging software and look for your device serial number (you may need to enable USB debugging on the phone). Click “Root” or “Debug” to begin rooting/debugging your device.
Step 2: Once the device is rooted/debugged, you can see the contents of the data partition. This is the partition on the phone where all of your data is stored, including files, photos, and contacts. You can now extract any information that you need from this partition.
Step 3: To exit debugging mode, press the power button and select “Power off.” Disconnect the USB cable and turn off the phone. Congratulations – you have successfully hacked a Samsung phone!
While exploiting system bugs to hack Samsung phones, you can send and receive all images and similar media between the device and your computer. This will allow you to keep track of all the information that was stolen during the hack. Remember, it is important to be patient and take your time while performing these steps – a successful hack requires precision and attention to detail.
How to Prevent Your Phone From Being Hacked?
There are several precautions and smartphone hacks to prevent your phone from getting hacked. These include:
- Always set complex passwords for your social media and bank account apps;
- Using a password manager to generate passwords for you;
- Never establish a Bluetooth connection with an unknown device;
- Don’t open malicious websites if they’ve been sent to you via text or email;
- Installing the latest security patches available for your device as soon as they’re released;
- Don’t install suspicious apps or malicious software from the play store or any third-party store. Only download apps from the official Play Store or App Store;
- As far as possible, avoid using public Wi-Fi networks or unsecured Wi-Fi networks.
Is It Possible to Hack a Phone?
Hackers often use mobile technology or malicious apps to hack people’s phones and listen to their calls or chats. One can also use an app like mSpy to access someone’s information on their phone.
Can Someone Hack a Phone with Just a Phone Number?
Yes, a hacker can easily hack into your phone with a phone number. They can use spy apps like eyeZy or use methods such as phishing to get you to reveal your login credentials. Once you give out this sensitive information, it can become extremely easy for hackers to get into your phone.
Conclusion
Learning how to hack a mobile phone has never been easier with these advanced methods. As you can see, there are many different ways to hack a phone and access sensitive data on it. While some methods are more effective than others, they’re often only possible if you’re an advanced hacker. However, if you want to hack someone’s cell phone, apps like mSpy or eyeZy are ideal for most users. They give you access to all the data on the target phone regardless of its operating system.
However, you must always remember that hacking into someone’s phone using malicious software or any other means is illegal. Always ensure to check your local laws before doing so.
Confusing. So many to download. Don’t know one from the other. Some are saying you have to have target phone. If I could get to his phone I wouldn’t need this. He has fingerprint, but I have code to get in.
If hacking was easy, everyone would do it 😉 Yes, you need access to the phone to install it.
Trying to decide what is the best way to get sms messages sent to my phone from a targeted phone
Try one of these: 8 Top-Rated SMS Tracker Apps for Android and iPhone (we prefer mSpy).
Hiya, so I received texts from another phone in my household. Luckily they were home at the time so I said why they were texting me- they said they didn’t. Has their phone or mine been hacked? I’m really paranoid now.
You said you’re not going to publish in depth info here about the attacks you mention as they aren’t beginer friendly. Do you have an article somewhere else that details how to carry out the others?
Such info is rather kept private.
Hello. My husband and I have been married for 12 years and have two wonderful kids together. But that doesn’t change the fact that I was told by a family member that he’s been having an affair with my little sister who is 25 years old. This is really hurting me and I really need to know if he is having an affair with her and if he has other ones besides her? Every time I ask him about he and my sister, he says I’m crazy. I can’t go on like this so I need to know if he is in fact sleeping with her or if I truly am completely going crazy and just paranoid. I can’t go on feeling like this, I have to get back to being the best mom my children used to know me to be. I feel like this affair has impacted my life for the worst and it’s just at a standstill. Please help me because I need to know once and for all, so I can get my life back on track and start my divorce! I would really appreciate your help and thank you for your time. Goodnight…
I enjoy reading through a post that can make people think. Also, thank you for allowing for me to comment!
Honestly I can’t imagine ⤴️ why anyone would dislike this , this is very clear and very helpful, kudos man you got a new shout out and recommended from me thank you very much time.